
REQUEST A DEMO
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
THREATNOTE
Threatnote is a Unified Threat Management Platform built to help security teams and MSSP's operationalize cyber threat intelligence. It brings together intelligence requirements, RFI workflows, dark web monitoring, digital risk protection, and threat hunting in a single modular system designed to scale with your team.
VIP Monitoring
Monitor for threats targeting executives and other high-profile individuals across the dark web and public sources.
Open-Source Intelligence
Collect and surface relevant intelligence aligned with your team's priority intelligence requirements, enabling action on what's most important to your stakeholders.
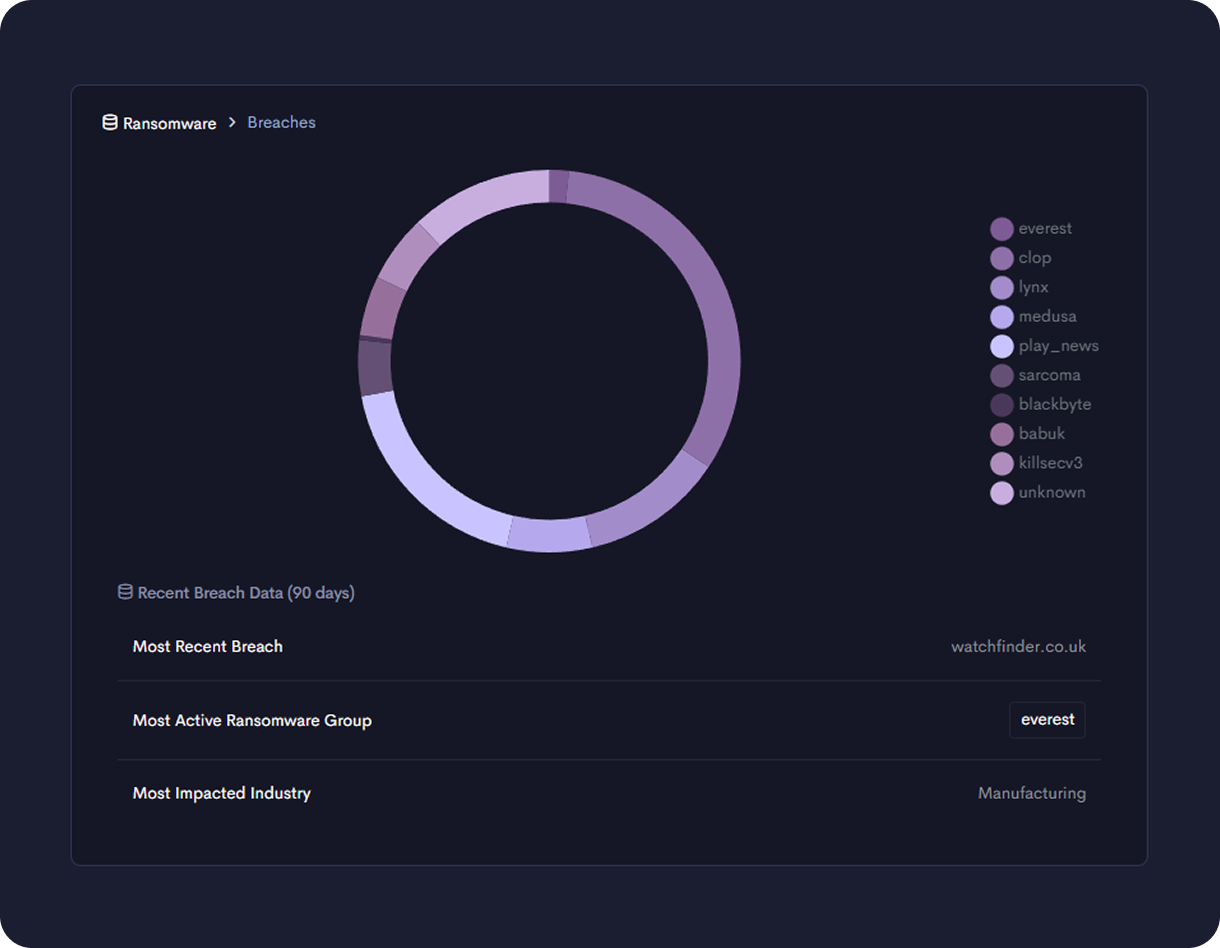
Dark Web Monitoring
Track exposed data, credentials, and threat actor chatter across dark web sources. Surface information relevant to your company to detect threats early, before they become incidents.
Vulnerability Intelligence
Identify high-risk vulnerabilities in the vendors and technologies most critical to your environment, with emphasis on those being actively exploited or with available proof-of-concept exploits.
Third-Party Intelligence
Monitor your vendors, partners, and suppliers for breaches, leaked credentials, and other risks that could impact your organization.
Brand Protection
Detect suspicious domains, fake mobile apps, and impersonating social media profiles targeting your brand, customers, or employees.
Intel Operations
Centralize your intelligence workflows with this module to manage RFIs, track PIRs, build reports, disseminate intelligence to stakeholders, and drive threat hunts, all in one place.
Attack Surface Intelligence
Gain visibility into exposed assets, misconfigurations, and vulnerabilities across your external attack surface to prioritize and reduce risk.